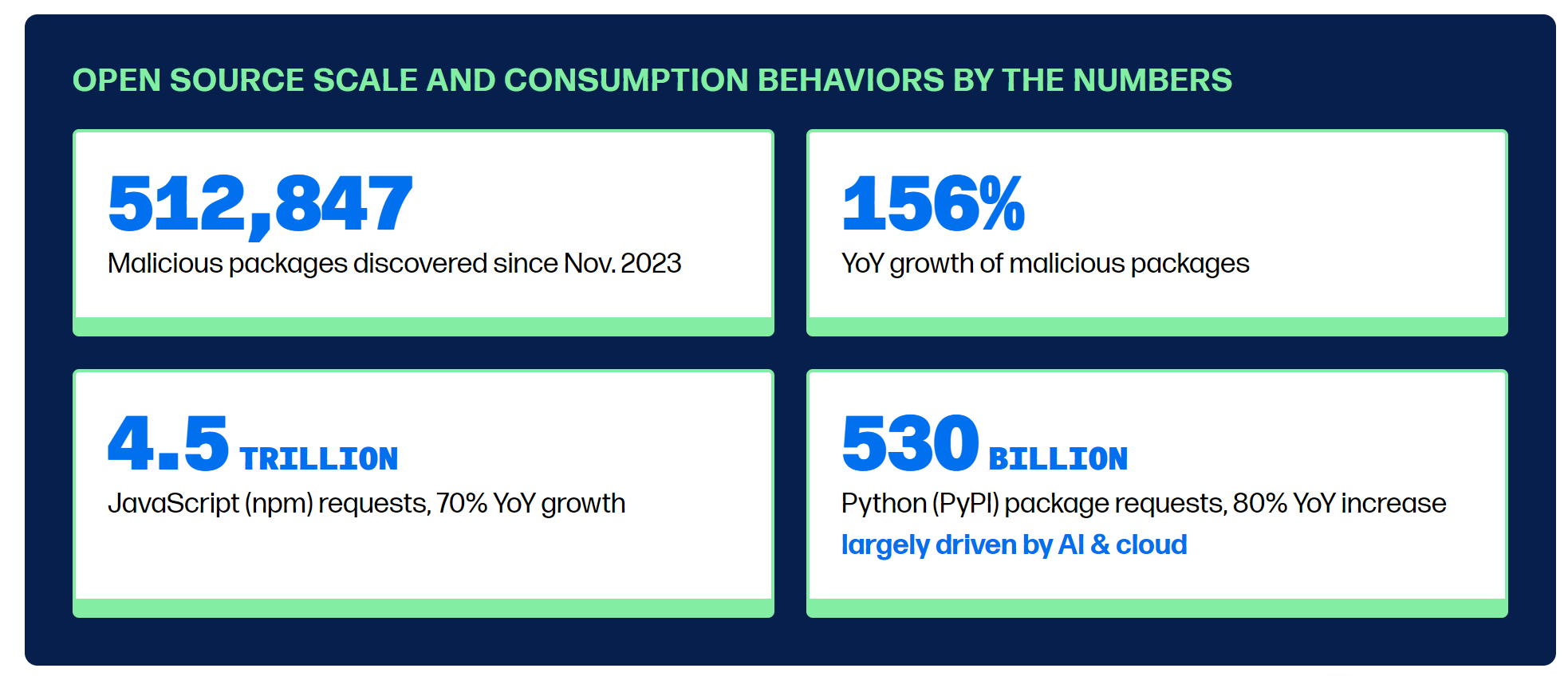
The number of malicious packages within the open-source ecosystem has surged dramatically over the past year, as highlighted by a recent report from Sonatype. Experts noted that the volume of malicious components deliberately uploaded to open-source repositories has increased by more than 150% compared to the previous year.
Open-source software, founded on a transparent development process that allows anyone to contribute, serves as the backbone of most modern digital technologies. Sonatype’s report analyzed over 7 million projects, revealing that more than 500,000 contained malicious components.
The issues surrounding vulnerabilities in open-source packages, and the challenges developers face in maintaining them, have gained heightened relevance in recent years in the wake of large-scale cyberattacks and exposed vulnerabilities. A recent example is an incident involving the data compression tool XZ Utils. Hackers had been attempting for years to introduce a vulnerability into the tool, with the aim of spreading it across numerous Linux servers worldwide.
Experts emphasize that the problem lies not only in the hacker attacks themselves but also in the approach of both publishers and consumers of open-source solutions. In the rush to release new versions and features, security measures are often neglected. As a result, critical vulnerabilities remain unaddressed for extended periods. For instance, it is known that even years after the Log4Shell vulnerability was discovered, around 13% of its downloads still contain vulnerable versions.
On average, it takes up to 500 days to patch critical vulnerabilities, far exceeding the previous timelines of 200 to 250 days. Less severe bugs take even longer to fix — in some cases, this process stretches beyond 800 days, whereas such durations rarely exceeded 400 days in the past.
These findings indicate that the software supply chain has reached a critical juncture, where the resources of publishers are simply unable to keep pace with the rising number of vulnerabilities. Furthermore, each programming ecosystem has its own particularities, which complicates security efforts. For instance, in recent years, the Node.js package manager has seen a sharp increase in malicious packages linked to spam and cryptocurrencies.


