Experts at Silent Push assert that the FIN7 group has resumed its activities after the United States declared the group’s dissolution in 2021.
In 2021, the United States announced that FIN7 no longer existed after key members of the group were sentenced. The U.S. Department of Justice described FIN7 as a criminal organization with over 70 participants, organized into distinct business units and teams. Since 2013, FIN7 has caused damages amounting to approximately $3 billion to various organizations.
It should be noted that in 2023, hacker attacks continued, albeit under different brands rather than as FIN7. FIN7 has been linked to ransomware families such as Black Basta, DarkSide, REvil, and LockBit.
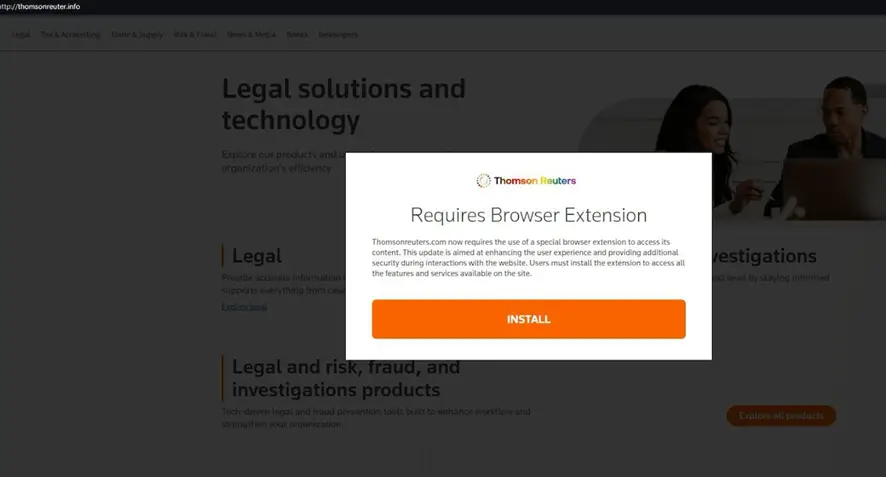
According to Silent Push, in 2024, FIN7 resumed its activities under its own name, creating thousands of websites impersonating various media and technology companies. The malicious domains were registered by a major hosting provider, Stark Industries Solutions.
The first signs of FIN7’s resurgence appeared in April 2024, when Blackberry reported a breach of a major automotive company. The attack began with the infection of users searching for a popular free network scanning tool.
Silent Push specialists developed a method to track FIN7’s rapidly expanding infrastructure, comprising over 4,000 hosts. The hackers employ various methods: from “typosquatting” and malicious advertising (malvertising) to harmful browser extensions and phishing domains.

FIN7’s domains target various major brands, including American Express, Bitwarden, Bloomberg, CNN, Dropbox, Google, Meta*, Microsoft 365, Midjourney, and others. Many domains appear as legitimate business websites, often with text from standard templates. This is done to artificially “age” the domains and give them a positive reputation. It took hackers 6-9 months to build up the infrastructure.
In typosquatting attacks, cybercriminals register domains that closely resemble those of popular software. Phishing domains are advertised on Google to appear higher in search results than the legitimate software sources. The software used as bait includes 7-zip, PuTTY, ProtectedPDFViewer, AIMP, Notepad++, Advanced IP Scanner, AnyDesk, pgAdmin, AutoDesk, Bitwarden, Rest Proxy, Python, Sublime Text, and Node.js.
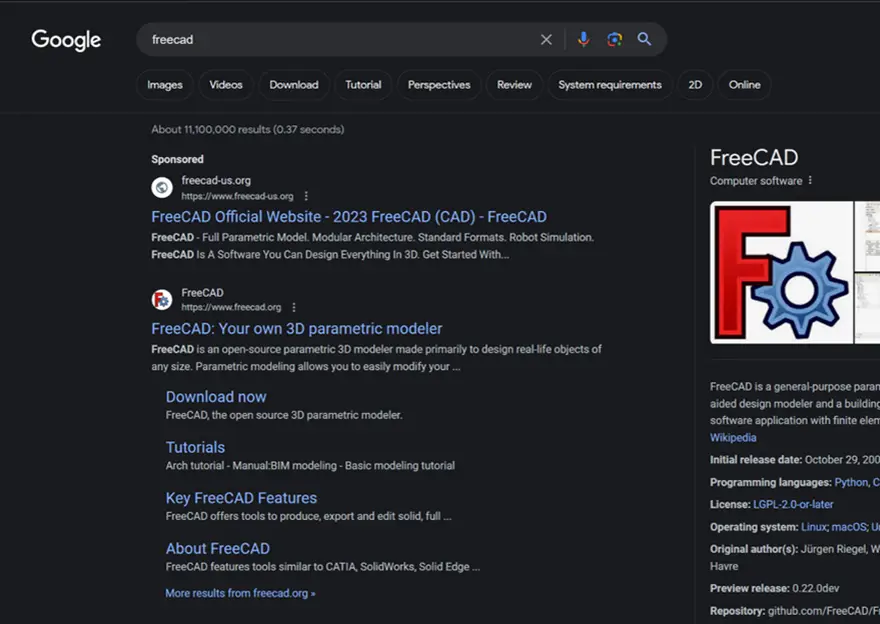
Silent Push discovered new FIN7 domains after a company that had been previously attacked by the group suspected their reactivation. The search for hosts revealed only one active site, which then led to numerous other FIN7 resources.
Previously, FIN7 operated through front companies in the cybersecurity sector, recruiting hackers to assist in ransomware attacks. One key member of the group was arrested after responding to a job posting from such a company.
Like other phishing groups, FIN7 exploits current global events. Currently, the hackers are targeting tourists attending the Olympic Games in France. Among the new FIN7 domains are several phishing sites selling counterfeit tickets to the Louvre.
According to Silent Push, the research clearly indicates that FIN7 has returned and is rapidly expanding. The company expressed hope that law enforcement agencies will take notice and implement additional measures, and that many competitors will be able to use the disclosed information to further their investigations into FIN7’s infrastructure.


