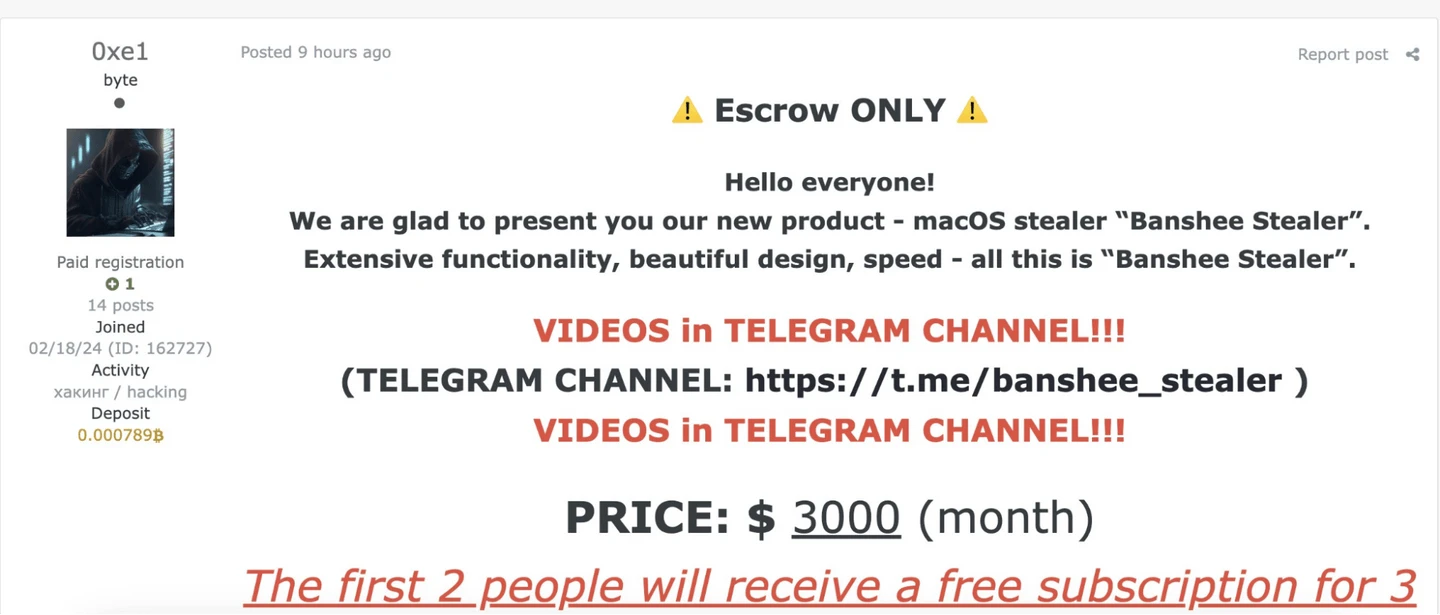
The developers of the Banshee Stealer malware have ceased operations following the leak of its source code online.
Banshee Stealer, which emerged in August 2024, distinguished itself as one of the few infostealers specifically designed to target macOS systems. However, it gained notoriety for its exceptionally high rental price—over $3,000 per month, roughly ten times the standard cost of similar programs.
According to a report by Elastic Security Labs, the malware possessed all the typical features of infostealers: stealing passwords from browsers, exfiltrating cryptocurrency wallet keys, collecting system information, and deploying phishing pages.
Experts suggest that the source code leak may have been the result of a dissatisfied client. Such incidents are not uncommon on hacking forums, where disgruntled buyers—feeling cheated or seeking to sabotage competitors—often release malware code into the public domain.
Recently, Elastic Security Labs identified a new method for distributing the GHOSTPULSE malware—embedding data within PNG image pixels. This technique is considered one of the most significant innovations in malware functionality since GHOSTPULSE first appeared in 2023.
Previously, GHOSTPULSE (also known as HIJACKLOADER and IDATLOADER) concealed malicious data within the IDAT blocks of PNG files. The new algorithm, however, allows malicious data to be embedded directly into the pixel structure of the image, significantly complicating detection efforts.


