Source: Infoblox
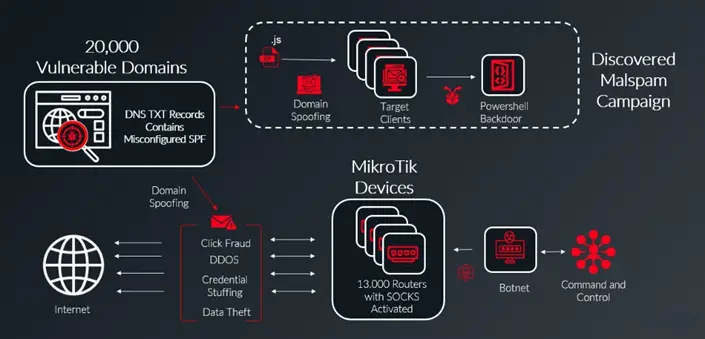
In November 2024, a network of 13,000 MikroTik routers was discovered exploiting a DNS misconfiguration vulnerability to bypass email security measures and deliver malware. Hackers leveraged a flaw in the configuration of SPF records, which are responsible for authorizing servers to send emails on behalf of domains.
Infoblox reported a campaign distributing malicious emails where attackers impersonated DHL Express. The emails contained invoices within ZIP archives, which included a malicious JavaScript script. Upon execution, the script initiated a PowerShell command to connect to a command-and-control (C2) server.
Approximately 20,000 domains were found to have overly permissive SPF configurations with the parameter “+all,” which allowed any server to send emails on behalf of the domain, effectively nullifying spoofing protection. To mitigate such attacks, experts recommend using the “-all” parameter, which restricts email sending to authorized servers only.
While the exact method used to compromise MikroTik routers remains unclear, Infoblox noted that devices running various firmware versions, including the latest, were affected. MikroTik devices are frequently targeted by hackers due to their robust capabilities, making them ideal for assembling large botnets.
In this newly identified botnet, infected devices were employed as SOCKS4 proxy servers to send phishing emails, execute DDoS attacks, steal data, and obfuscate traffic, enabling thousands of compromised machines to conceal the origin of malicious activities. Experts strongly advise immediately updating router firmware, changing default administrator passwords, and disabling remote access to management panels if unused.
In the summer of 2024, OVHcloud reported a record-breaking DDoS attack with an intensity of 840 Mpps, orchestrated via a MikroTik botnet. Despite recommendations to apply firmware updates, the slow adoption of patches leaves many devices vulnerable for extended periods.


