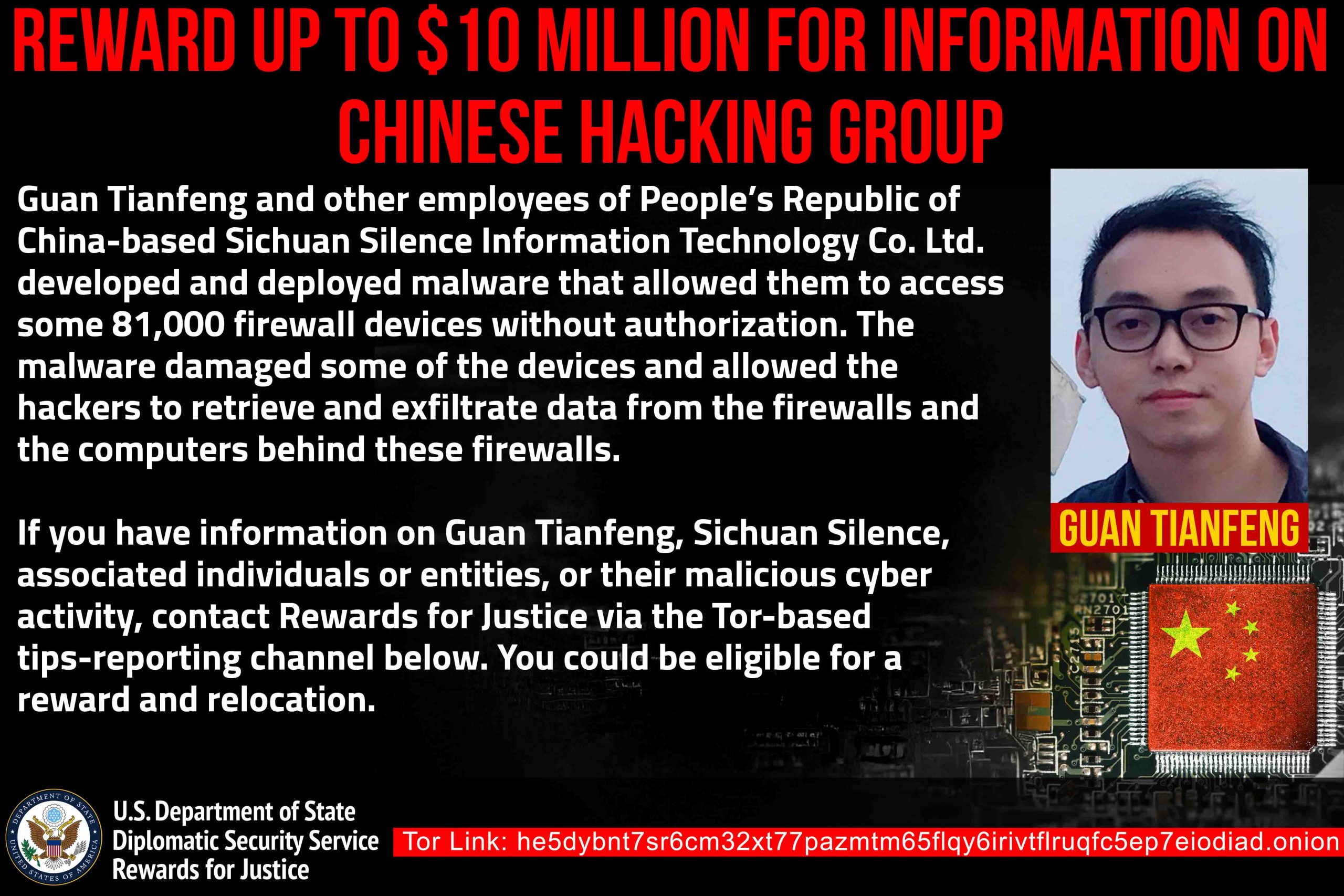
The United States Department of the Treasury has imposed sanctions on the Chinese company Sichuan Silence and its employee for orchestrating ransomware attacks using the Ragnarok malware. These 2020 attacks targeted critical infrastructure in the United States and other nations.
Sichuan Silence, based in Chengdu, operates on behalf of Chinese government entities, including intelligence agencies. The firm specializes in hacking computer networks, password cracking, email surveillance, and suppressing dissenting opinions.
The company’s employee, Guan Tianfeng, identified a vulnerability in a firewall and exploited it to infect approximately 81,000 devices worldwide. The objective of these attacks was to steal login credentials and deploy the Ragnarok ransomware. In the United States alone, more than 23,000 devices were compromised, including 36 safeguarding critical infrastructure. Among the victims was an energy company, where the attack, if not mitigated, could have led to catastrophic consequences.
The U.S. Department of Justice has filed charges against Guan, and the State Department has announced a reward of up to $10 million for information leading to the identification or apprehension of Guan or Sichuan Silence.
The attacks exploited an SQL injection vulnerability (CVE-2020-12271, CVSS score: 9.8) in Sophos XG firewalls. The hackers developed tools enabling root access to devices, data extraction, and hardware damage. The malware employed in the attacks was dubbed the Asnarök Trojan.
Sophos promptly detected the issue, released patches, and removed the malicious files. However, the attackers had implemented a “kill switch” capable of triggering Ragnarok ransomware on victims’ networks. Sophos investigators were able to trace the attacks back to Sichuan Silence’s research institute in Sichuan.
Following the sanctions, U.S. companies and individuals are prohibited from conducting business with Sichuan Silence or its employees. The company’s assets within the U.S. will be frozen, and financial institutions working with Sichuan Silence risk incurring penalties.
In 2021, Meta removed over 600 Facebook and Instagram accounts linked to Sichuan Silence. These accounts were used to disseminate COVID-19 misinformation targeting audiences in the United States, the United Kingdom, Taiwan, Hong Kong, and Tibet.
In November, Sophos concluded an extensive investigation into attacks by Chinese groups that have systematically targeted network devices worldwide for over five years. This series of attacks began in December 2018, when hackers exploited weak security configurations to access a device at the Indian branch of Cyberoam. Using network scans, they discovered additional vulnerabilities, ultimately leading to the Asnarök flaw in 2020.


